DATACENTER
Should We Confine Data Within Borders?
FEBRUARY 18, 2016 / BY MEHDI PARYAVI
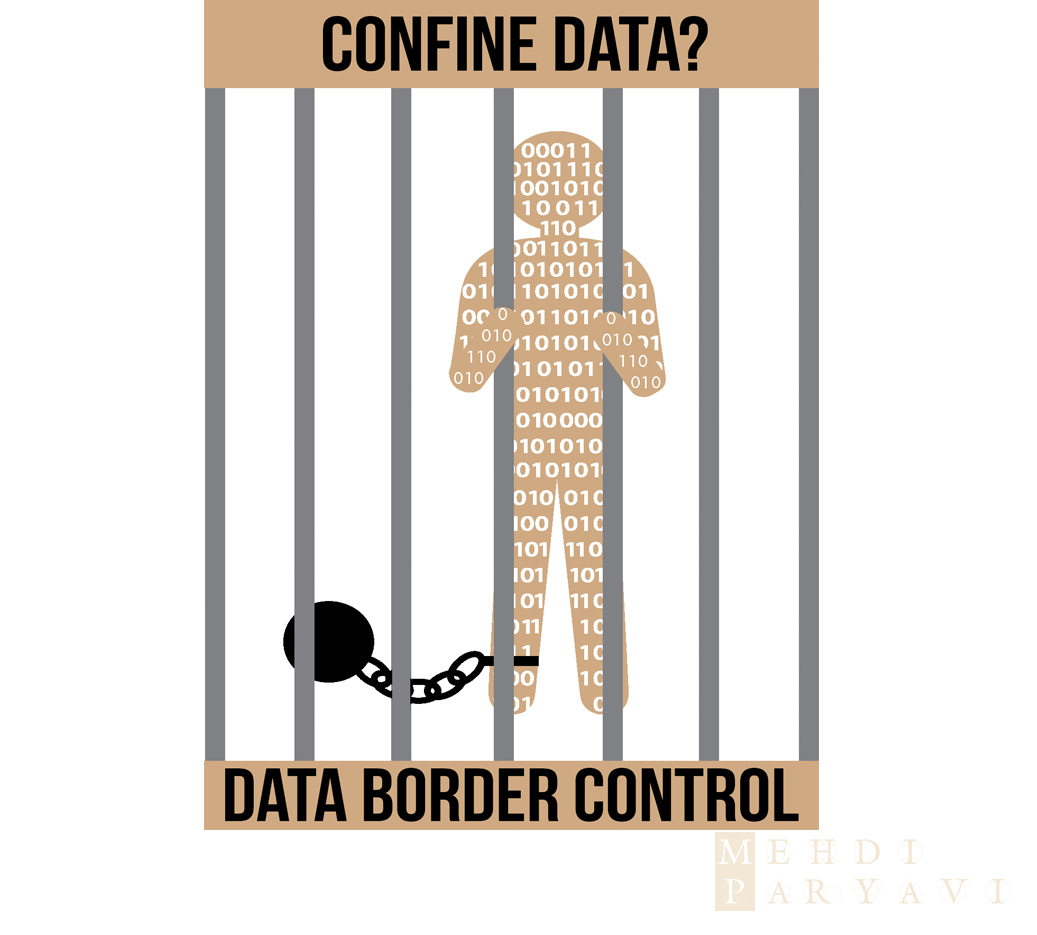
When liberal economy and trade meant traveling between borders, creating the Russia’s Iron Curtain or Germany’s Berlin Wall seemed like a political remedy to safeguard certain sociopolitical hemispheres. But those latter policies and the erection of those barriers were proven disastrous to their citizens and the world around them.
Looks like history has to repeat itself no matter what. Recently Russia announced that Russia’s data must stay in Russia. In the United States, we have strict rules governing data safekeeping within our borders for industries like healthcare, finance, etc. Are these practical policies? Can these policies be sustained in the revitalizing information age? How can Cloud impact—or be impacted—by these policies?
Without going any further, let us bluntly say that data cannot be confined within borders. Though data is more valuable, it is not equivalent to gold in terms of tangibility, that can be transported on the back of trailers and stored in Fort Knox. Before banks were invented, people kept their money under their pillows. But as soon as money started to be deposited in banks, people practically lost tangible control over it and transactions among banks became a vivid norm. When we say we want to keep our data within our borders, it is synonymous to saying that we want to keep our money under our pillow. For as long as data is kept in paper copies, the concept of keeping physical borders can be practiced. But as soon as data is digitized, we encounter an entirely different realm of realities.
If we put too much focus on physical security, we will lose its availability sooner or later.
What’s critical about digitizing data is that—as intangible as it is—if we put too much focus on physical security, we will lose its availability sooner or later. When data is transformed into a logical being, it must be kept secure and dealt with in its logical form. Storing data in data centers that are within the circle of our trusted allies goes a long way in securing our own interests. That’s what allies are for. We have traditionally exchanged goods, services and knowhow with our trusted allies. Now information is a key substance that must be physically trusted abroad while being logically secured at the home base.
The IRS hack of 2015 was a national disaster that happened with the breach of the confines of the cyber world—it was not a physical border sabotage. The 2014 hacking of Target following Black Friday, which affected 110 million customers, didn’t happen by an American in the United States. It ensued out of Russia (by a 17-year old) under the watch of a security team situated in Bangalore, India. This denotes that regardless of their race, gender, age or location, hackers don’t first search for the location of your data center to see if your physical location matches their jurisdiction and citizenship before initiating an attack. It means that your data does not need to be in Russia to be hacked by a Russian or vice versa. By the same token, due to the intangible and borderless nature of data, Target for example, didn’t mind their security team to be manned out of India.
It is critical to understand that the nature of data, once it is digitized, is logical—not physical. Therefore, any extent of physical fortification is futile in the sense that it doesn’t address the natural essence of what it is trying to protect. On the contrary, we could reverse this cross-border liberation to our advantage if we built clouds of physical locations around the world and seeded vital data globally in an arrangement so that theft at a physical data center node, at any given location (even the IRS’s main infrastructure), would not provide criminals with access to the logical data they seek. Thus, we could be using this diversity of locations to our security benefit. Security professionals must give this point a serious thought…
We could be using this diversity of locations to our security benefit.
Today, life revolves around information and whatever that goes along with it. This means that when you travel you want your information to securely travel with you. So, our great minds of data integrity and security must work on key remedies for the root-cause of the problem—that is establishing data security, not putting physical borders around a substance that knows no physical borders.
Establishing actual data security is key, not attempting to place borders around a substance that knows no physical boundaries.
Total information security will only be achieved if we can finally merge the physical aspects of data with its logical, and leverage its physical diversity to cultivate dynamic logical security that would be impossible otherwise. Ultimately, cyber criminals will walk into a total darkness from which they would not be able to make sense or conclude with legitimate information. This is a security state which can best be described by a piece from the world-renowned poet and mystic, Rumi:
“SOME Hindus had brought an elephant for exhibition and placed it in a dark house. Crowds of people were entering into that dark place to see it. Finding that ocular inspection was impossible, each visitor felt it with his palm in the darkness. The palm of one fell on the trunk. ‘This creature is like a water-spout,’ he said. The hand of another lighted on the elephant’s ear. To him the beat was evidently like a fan. Another rubbed against its leg. ‘I found the elephant’s shape is like a pillar,’ he said. Another laid his hand on its back. ‘Certainly this elephant was like a throne,’ he said. The sensual eye is just like the palm of the hand. The palm has not the means of covering the whole of the essence. The eye of the sea is one thing and the foam another. Let the foam go, and gaze with the eye of the sea. Day and night foam-flecks are flung from the sea: of amazing! You behold the foam but not the sea. We are like boats dashing together; our eyes are darkened, yet we are in clear water.”
Mystic interpretations and true intentions of this narrative aside, game-changing content/data protection philosophies and methodologies could be derived from this divine reality.
The world we live in has become so impractical simply because we are on the verge of adopting the information technology—the extent and breadth of which we are yet to understand. We are using modern-day information technology assets and applications hosted in billion-dollar data centers, but are following the governing policies that were relevant for when we were dealing with pen and paper. There must come an awakening of realities that the governance of pen and paper traditions over digital media will fail with catastrophic consequences.
Blunt Doses of
Data Center Knowledge
WELCOME!
Often I am asked to provide the data center community my points of view to the whole data center ordeal. Obviously data center is a focal expertise of mine. But life is not all about one’s field of work. Our educational system, political arena, economic challenges, diverse cultures and norms within and around us, depict the very atmosphere we live in. So there is a lot to be said about the above and more. But let’s start with data centers and see where it takes us…

... "Values of the past are the poetry of our time" ... - M.P.
... "To be or not to be, is not the question. The question is how to be." ... - M.P.
... "Our past is affected as much as our future with the implications of our present." ... - M.P.
.png)